Just as in the movie, “The NeverEnding Story,” where young Bastian Bux is tasked with saving the land of Fantasia from the threat of The Nothing, cybersecurity is a never-ending threat to public agencies of all sizes.
Technology goods and services are making daily advances, and so are the methods of cyberattacks. The threats are constantly evolving, making it difficult for individuals and agencies to keep up. Cybercriminals continuously find new ways to exploit vulnerabilities and gain access to sensitive information. If only we had Falkor in the real world…
Cybersecurity is a Team Quest
Since we don’t have Falkor to help us fend off the constant barrage of potential attacks, the task of keeping agency data and systems secure is up to the individuals in the public agencies, whether they’re IT people or not. However, the proposition of cybersecurity can seem a little daunting for the average user in the face of the moving targets that are cyber threats. To combat this, public agencies should incorporate regular cycles of cybersecurity training into their employee training programs, and that cybersecurity training should include the agency’s most current policies on:
- Document management
- Password management
- Unauthorized software installation
- Email usage
- Social media usage
- Internet usage
- Company data protection
NASPO offers free courses in our Procurement U catalog that can be incorporated into agencies’ training programs; check out our courses on How to Protect Your Data and How to Protect Yourself Against Phishing Attacks.
The Threat You May Know
It is in the best interest of agencies to ensure that their security strategies are also consistently evolving and never-ending to match the level of cyber threats. It’s not a “set it and forget it” type of situation anymore; there are far greater threats than a strange email offering some dubious prize. Sometimes, the newest threat can come from products the agency and its users are already familiar with. Back in May, Google released eight new top-level domains (TLDs) that became available for public registration. Normally, that would just be a bit of info that the average user wouldn’t necessarily know or care about, except that two of the new TLDs are already common Windows and Apple file type extensions: .zip and .mov.
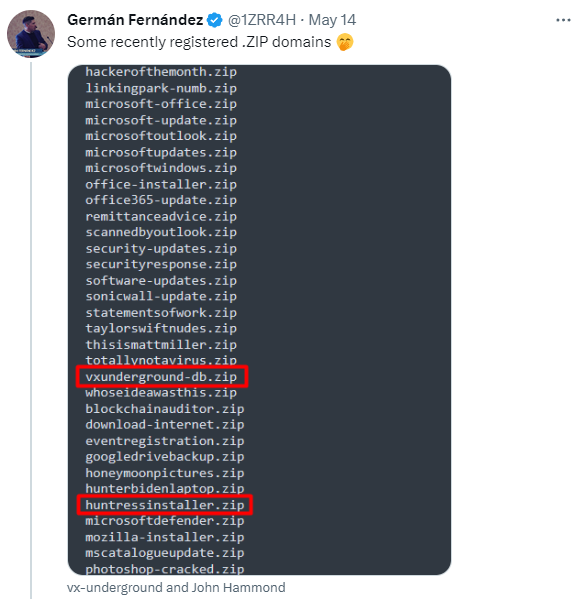
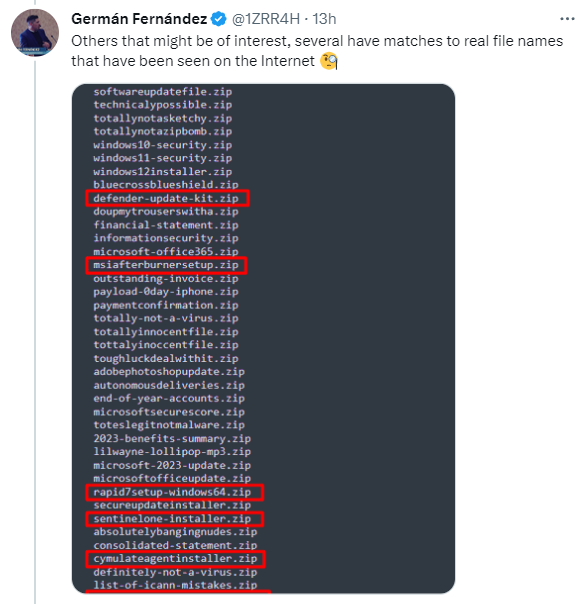
ZIP files are a format that contains multiple files that have been combined and compressed to a smaller file size. MOV files are Apple QuickTime movie files. The potential for a cyber threat arises because now, anyone can register a public website using either .zip or .mov as its domain name (e.g., vacationpics -dot- zip), and it will appear to be a harmless file, but the website may contain malware that activates automatically upon the website being visited. If a criminal wanted to target an agency for an attack, they could simply send an official-looking email from a spoofed email address to all of the agency’s users that contains a link to something that the user would assume is a file; they would not guess that it’s actually a website. Plenty of users would not dare click anything sent to them in an email, but it only takes one person to fall for the scheme. Additionally, anyone who even types out what they think is a file name that contains a .zip or .mov file extension could inadvertently be linking to a malware website. Cybersecurity experts who are monitoring this issue have noticed that there are many new domain name registrations that have clearly been created with malicious intent:
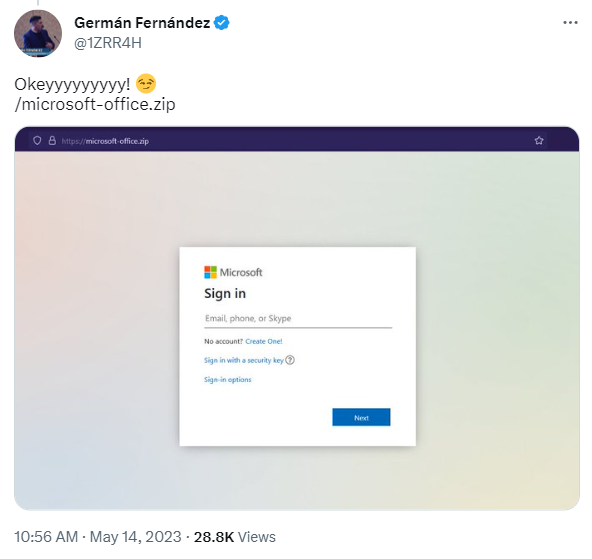
It also means that anywhere those file type extensions are saved as plain text (in an old MS Word document or in Windows Explorer, for example), that text could now resolve as a link to a malicious website. For example, this is a screenshot of the website that comes up for what might be a common file in the average user’s Windows Explorer screen, Microsoft -dash- Office -dot- zip:
(The preceding text is not typed out in standard website format, so as not to form a link.)
Some cybersecurity experts are recommending that IT departments indiscriminately block all domain names that end with .mov or .zip from within the agency’s internet or intranet sites. If you’re unsure whether or not it’s on your agency’s radar, perhaps it’s a discussion worth having with your agency’s IT staff. The Chief Information Officer (CIO) and/or Chief Information Security Officer (CISO) will likely want to review the current policies and make the appropriate next-step determination.
Manage Your Risk
With that example in mind, it is also in agencies’ best interest to change the way they think about cybersecurity. It’s no longer prudent to just try to avoid the failures in systems and/or installed software; it is an inevitability that should be expected and planned for as a part of an overall risk management strategy incorporated into cybersecurity procedures. One strategy that public agencies can use is to follow the example of the U.S. government and implement zero-trust architectures, which assume that all systems can or will be compromised. For more strategies on how agencies can update and expand their cybersecurity processes in the face of ever-changing technology, check out this Harvard Business Review article that includes three ways to improve your cybersecurity.
Cybersecurity is like laundry: it’s a process that will never actually be totally complete.